- Norton Power Eraser For Mac
- Norton Power Eraser Not Working
- Norton Power Eraser Free Download
- Norton Power Eraser Windows 7
Norton Power Eraser (NPE) is a small portable executable which uses Norton Insight in-the-cloud application ratings to scan a computer system. The program matches an application found on the user's computer with a list of trusted and malicious applications. This video guides you on how to download and run Norton Power Eraser 6.0 and remove online threats.For more help: www.support.norton.com. Jul 22, 2021 Norton Power Eraser 5.3.0.115 on 32-bit and 64-bit PCs. This download is licensed as freeware for the Windows (32-bit and 64-bit) operating system on a laptop or desktop PC from antivirus without restrictions. Norton Power Eraser 5.3.0.115 is available to all software users as a free download for Windows. Filed under: Norton Power Eraser Download. Sep 11, 2018 Symantec Norton Power Eraser wipes out threats that get past your antivirus, or that prevent antivirus installation. It's not meant to be a full-scale antivirus; you use it when you need powerful.
Its purpose is to scan your computer and eliminate aggressive threats that are usually tough to remove by traditional security software. You can think of it as an extra tool that strives to improve the malware cleanup results, regardless of the security suite you run on the system.
Program toko ipos 4 keygen softwares for pc. Norton Power Eraser is absolutely free of charge and does not require installation – simply double-click the executable to deploy it.
The application is not a scanner per se, because it relies on Symantec’s file reputation service, Norton Insight. This means that having an Internet connection is a mandatory requirement for the program to carry out its job.
As soon as started, the license agreement needs to be accepted (we went through his process at each launch) in order to move forward with the application.
The interface of the application is simple and to the point. It features simple options that let you start scanning the system for security risks, check the history of previous findings or access a small set of advanced options.
A computer restart is mandatory for carrying out the scan activity because Norton Power Eraser also checks for rootkits by default. When the system is back online, you can see the files currently verified. On the downside, there is no indication about the completion time for the task, or a bar to hint at the progress.
After the scan, all items deemed as a threat as well as the suspicious ones are presented. For the first ones there is only one action available: remove. Given the aggressive nature of the program, it may flag perfectly legitimate files as malicious, so a double check from your part makes for a great idea.
That’s why this is not a tool recommended for beginner users, but for those that can discern between good and bad files. This flaw is highlighted by Symantec.
During our tests, Norton Power Eraser managed to uncover a small batch of threats, but it also picked up a couple of legitimate files. Luckily, should you be on the fence with removing an item, the program’s default action before fixing up the computer is to create a system restore point. It does take a while longer to complete the cleaning but it is also the safest way.
World atomic clock sync for mac. Another way to recover false positives is to check the history of the session. Norton Power Eraser offers the possibility to revert the deletion process and restore the files.
Before dumping the threats, you can take a look at the file reputation details. The information available includes the date when the file was first identified and when it was last used.
Under the advanced section of the application you’ll find more scan options that can target various areas of the computer. You can run a reputation scan on a specific file or folder or check the entire system for malicious files.
The third option choice is multi-boot scan, which is reserved for multi-boot computers. However, in our case, the application could not identify Windows 8 as an additional operating system, available at boot time.
The configuration panel is as simple as possible. It provides options for setting up network proxy and lets you instruct the program to show only the bad files as well as disable multi-boot check and rootkit scan, although the latter is not recommended.
Norton Power Eraser is fast, which is to be expected from a scanner that relies on file reputation, and the results can be impressive; in our case, it managed to spot and eliminate about 450 threats out of a total of about 1000 we had for testing purposes.
The Good
All it requires is an Internet connection to link up with Symantec’s file reputation database. No installation is necessary and you can use it to check for rootkits as well as scan any file or folder on your computer.It automatically creates a restore point before eliminating the bad files. Also, there is the possibility to restore deleted files.
The Bad
The Truth
Computer restarts are required for scanning for rootkits, eliminating threats or restoring false positives. Despite all this,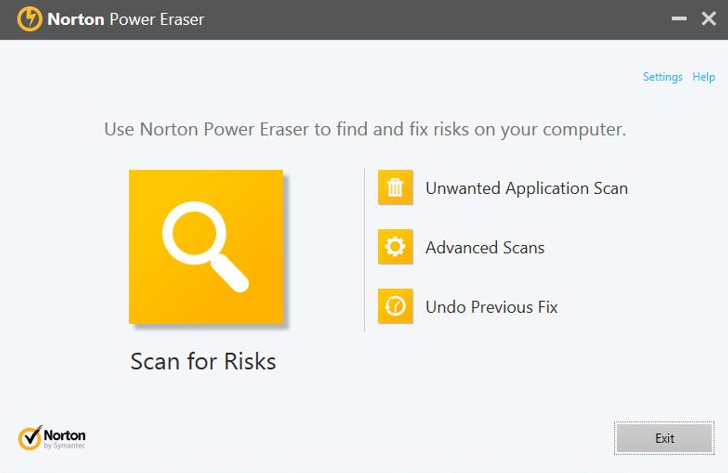 Norton Power Eraser
Norton Power EraserNorton Power Eraser For Mac
is a very good companion, regardless of the anti-malware suite you have on the computer.It relies on file reputation details, which makes scanning extremely fast. However, it is not to be used as a standalone security solution.
Its purpose is to scan your computer and eliminate aggressive threats that are usually tough to remove by traditional security software. You can think of it as an extra tool that strives to improve the malware cleanup results, regardless of the security suite you run on the system.
Norton Power Eraser is absolutely free of charge and does not require installation – simply double-click the executable to deploy it.
Norton Power Eraser Not Working
The application is not a scanner per se, because it relies on Symantec’s file reputation service, Norton Insight. This means that having an Internet connection is a mandatory requirement for the program to carry out its job.
As soon as started, the license agreement needs to be accepted (we went through his process at each launch) in order to move forward with the application.
The interface of the application is simple and to the point. It features simple options that let you start scanning the system for security risks, check the history of previous findings or access a small set of advanced options.
A computer restart is mandatory for carrying out the scan activity because Norton Power Eraser also checks for rootkits by default. When the system is back online, you can see the files currently verified. On the downside, there is no indication about the completion time for the task, or a bar to hint at the progress.
After the scan, all items deemed as a threat as well as the suspicious ones are presented. For the first ones there is only one action available: remove. Given the aggressive nature of the program, it may flag perfectly legitimate files as malicious, so a double check from your part makes for a great idea.
That’s why this is not a tool recommended for beginner users, but for those that can discern between good and bad files. This flaw is highlighted by Symantec.
During our tests, Norton Power Eraser managed to uncover a small batch of threats, but it also picked up a couple of legitimate files. Luckily, should you be on the fence with removing an item, the program’s default action before fixing up the computer is to create a system restore point. It does take a while longer to complete the cleaning but it is also the safest way.
Another way to recover false positives is to check the history of the session. Norton Power Eraser offers the possibility to revert the deletion process and restore the files.
Before dumping the threats, you can take a look at the file reputation details. The information available includes the date when the file was first identified and when it was last used.
Under the advanced section of the application you’ll find more scan options that can target various areas of the computer. You can run a reputation scan on a specific file or folder or check the entire system for malicious files.
The third option choice is multi-boot scan, which is reserved for multi-boot computers. However, in our case, the application could not identify Windows 8 as an additional operating system, available at boot time.
Rocky marathi full movie download. The configuration panel is as simple as possible. It provides options for setting up network proxy and lets you instruct the program to show only the bad files as well as disable multi-boot check and rootkit scan, although the latter is not recommended.
Norton Power Eraser is fast, which is to be expected from a scanner that relies on file reputation, and the results can be impressive; in our case, it managed to spot and eliminate about 450 threats out of a total of about 1000 we had for testing purposes.
The Good
All it requires is an Internet connection to link up with Symantec’s file reputation database. No installation is necessary and you can use it to check for rootkits as well as scan any file or folder on your computer.It automatically creates a restore point before eliminating the bad files. Also, there is the possibility to restore deleted files.
Norton Power Eraser Free Download
The Bad
The Truth
Computer restarts are required for scanning for rootkits, eliminating threats or restoring false positives. Despite all this, Norton Power EraserNorton Power Eraser Windows 7
is a very good companion, regardless of the anti-malware suite you have on the computer.It relies on file reputation details, which makes scanning extremely fast. However, it is not to be used as a standalone security solution.